Industries We Serve
At Cleard Life we understand the priority of hiring the right candidate
Limitless Applications
It’s time to explore the options

Augmented Intelligence
The Cleard.Life AI platform is a world first, developed by industry leaders to solve the challenge of avoiding bad hires and biased decision making in the recruitment process.

We Can Help
Whether you are a government department, a large corporate, SME or a small start-up, your personnel decisions need to be compliant, robust, commonsense, affordable and fast.

Protect Your Reputation
The implications can be catastrophic for organisations that serve ‘at risk’ members of society, manage critical infrastructure, handle personally identifiable information (PII), or have untrustworthy insiders.

Applications Galore
Perform threat vulnerability assessments, cyber audits on personnel, tender / third party / M&A due diligence.

Government Sector
We have extensive experience assisting government with the screening and vetting of candidates.
We were an inaugural panel member of the Australian Government Security Vetting Agency (AGSVA) in 2010. Our team continues to work alongside of the Australian government to conduct national security clearances to keep Australia safe.
Local and state government departments can vet staff for any ‘position of trust’ in a streamlined and consistent way, without duplication of existing processes. We also work with procurement teams by checking the background of shortlisted Tenderer’s key personnel – at no cost to the procurement team – which drives efficiencies and effectiveness of the due diligence process. Read more here 1> 2> 3>
The Australian Electoral Commission (AEC) employs 80,000 temporary workers. State Electoral Commissions also employ large numbers of citizens for a very short periods of time. Foreign influence in our democracy is at an all-time high but currently this element is not being checked adequately. Contigency workers for ABS Census (17,000) and MyHealth Record (900,000 users) have access to commonwealth resources and need to properly screened. Read more here 1> 2>
Business Sector
Cleard Life works alongside businesses of all shapes and sizes. With more than 85% of companies experiencing a cyber breach in the past three years, and some research suggesting 44.5% of breaches being caused by malicious trusted insiders. Trust is the new commodity and making sure, really sure, you have a trusted workforce makes business sense. Scalable plans means that we assist small businesses to make sound decisions as well as having the capacity to help with the customised screening needs of larger corporations. Recruitment agencies can add value by offering their clients the most comprehensive suite of background screening solutions on the market. Read more here 1> 2> 3> 4> 5>


Community Services Sector & Not for Profits
Cleard Life’s unbiased, in-depth screening process is a perfect fit to help organisations that assist ‘at risk’, ‘disadvantaged’ or ‘young’ members in our society. 1 in 6 Working With Children Check (WWCC) Card holders having a criminal history record that is deliberately not investigated by WWCC authorities. You can agree with Royal Commissioners not to solely rely on that check and truly protect the vulnerable you serve and your reputation.
This includes government and private sector facilities that work with the aged, people with disabilities, in children services and schools.
Taking care of the young and vulnerable in Australia’s society is of the utmost importance. Trust Cleard Life to make sure your volunteers and staff have cleared lives. Read more here 1> 2> 3> 4>
Cyber Risk Audit
Around 34% of breaches involve malicious internal actors (not fat finger or clicking on a bad link). 59% of organisations have experienced at least one malicious insider attack over the last 12 months. The inclusion of an assessment of personnel in a cyber security assessment increases the value of the entire audit. It offers an unprecedented, deeper and more comprehensive understanding of an organisation’s threat surface. By using government vetting standards together with red/amber/green quantitative results, the audit aids the security posture and establishes a baseline level of cyber hygiene. Insurance companies see value, too, as they can better determine the likelihood of a malicious attack caused by an insider threat actor. Read more here 1> 2> 3> 4>

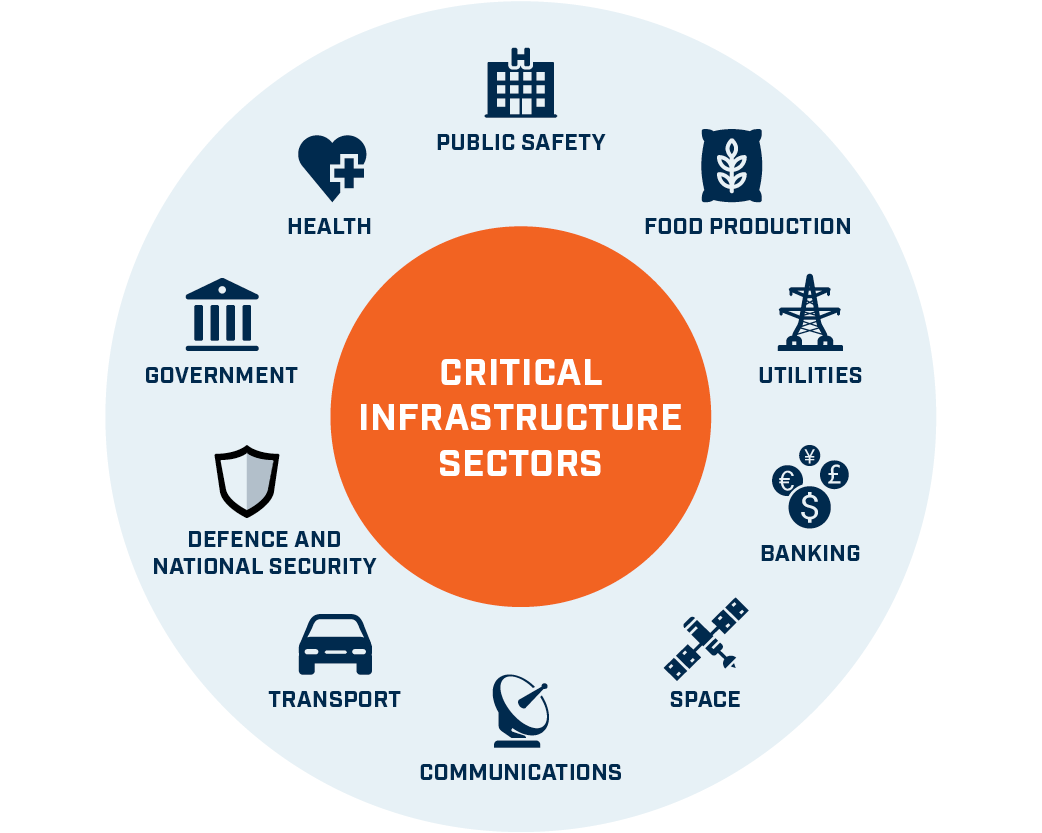
Australia’s critical infrastructure
If you are an owner or operator in the telecommunications, electricity, gas, water and ports sectors, to name a few, then we can help you identify the risks of sabotage, espionage and coercion in your workforce as you manage evolving national security risks. A police check will not do. Existing Critical Infrastructure Centre practice and new framework and legislation changes involve people risk. We have developed the first ever Critical Infrastructure Clearance to provide essential information on your workforce (and supply chain) via background checking & personnel security risk assessments. Read more here 1> 2> 3> 4> 5> 6> 7> 8>
ISM Compliance
The Australian Government, through the Australian Signals Directorate, Australia Cyber Security Centre produced the Information Security Manual. Compliance to Cyber Security Principle P10 is required. “Only trusted and vetted personnel are granted access to systems, applications and data repositories.” The ISM’s Guidelines for Personnel Security’s Security Control 0434 “Personnel undergo appropriate employment screening, and where necessary hold an appropriate security clearance, before being granted access to a system and its resources.” This appropriate, trusted vetting and screening entails more than a $50 police check, a ref check and ID check. We can assist you with your non-security clearance PSPF12 & PSPF13 compliance, vetting and personnel security measures. Read more here 1> 2> 3> 4> 5>


Retail Sector
The Australian Retailers Association estimates all forms of shoplifting (aka shrinkage) costs retailers $9.5B per year or 1-3% of gross profit. However the Theft Barometer 2020 also notes employee theft contributes between 50% and 81% of all shrinkage. Employees who embezzle are trusted members of the company’s team and it can be incredibly devastating to find out they have been ripping you off. Amplify your company’s screening program to deter & detect malicious trusted insiders, reduce your retail risk losses, improve your HR hygiene, security posture and bottom line. Read more here 1> 2> 3>
Defence Industry
With or without a security clearance, it is important to verify that your workforce is not filled with unmitigated risks. Enhancing your human resource practices can deter and detect trusted insider hostile acts. We are a DISP L3 Member and the first to be approved to sponsor, facilitate and manage national security clearance portfolios, up to NV2. The ANAO Audit of the clearance process indicates that complex cases take on average 640 days (NV1). Reduce the risk of a bad hiring decision. Reduce the ‘doubt and delay’ of an official security clearance outcome. Make your process more streamlined, more harmonised – in short: faster, better and nimbler. Read more here 1> 2> 3> 4> 5>


Mining Industry
Sexual allegations in mining worksites are a blight on the reputation of the whole industry. One of the biggest suggestions for policy change discussed in a recent inquiry was whether an industry-wide register of sexual harassers should be developed so offenders cannot move between companies. It is a complex area but we tackle sexual harassment head on, one mining company at a time. Our sector specific “CL-M” answers the ‘how to’ report, ‘when to’ report and ‘who to report to’. Our deep, fair and fast background screening practices are second to none. Read more here 1 >
Health Sector
Personal Health Information is the some of the most precious pieces of information an individual can ever hold, nothing is more personal than what blood type you are, your diagnosis, pathology history and your DNA. However, 78% of healthcare providers have experienced at least one data breach. Data breaches orchestrated by malicious trusted insiders, distinct from accidental breaches, present a profoundly damaging scenario. This represents 1 in 4 of all breaches and is proven to be the most expensive type of data breach. Read more here 1 >
