How to implement and navigate the Critical Infrastructure Personnel Security Rules.
The mandatory Critical Infrastructure Risk Management Plan (CIRMP) for critical infrastructure assets will increase security obligations for Critical Infrastructure Entities & “systems of national significance”. CIRMP obligations will require entities to (a) identify hazards for which there is a “material risk” that the hazard will impact their business operations, (b) minimise the material risks of those hazards occurring and (c) mitigate the impacts of hazards on the operation of their critical infrastructure assets. The identification of hazards that are a “material risk” will include all hazards – from natural disasters to cyber threats to insider threats. Here’s the specific rules for personnel hazard risks.
Rule 2 – Personnel hazards
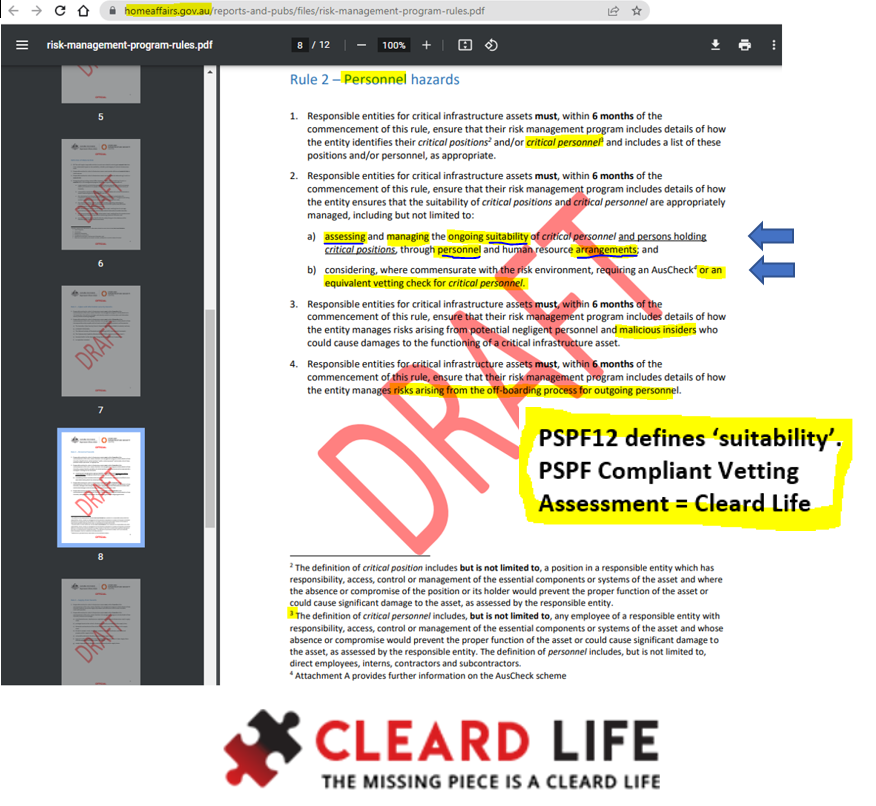
1. Responsible entities for critical infrastructure assets must ensure that their risk management program includes details of how the entity identifies their critical positions and/or critical personnel and includes a list of these positions and/or personnel, as appropriate.
2. Responsible entities for critical infrastructure assets must ensure that their risk management program includes details of how the entity ensures that the suitability of critical positions and critical personnel are appropriately managed, including but not limited to:
a) assessing and managing the ongoing suitability of critical personnel and persons holding critical positions, through personnel and human resource arrangements; and
b) considering, where commensurate with the risk environment, requiring an AusCheck or an equivalent [?] vetting check for critical personnel.
3. Responsible entities for critical infrastructure assets must ensure that their risk management program includes details of how the entity manages risks arising from potential negligent personnel and malicious insiders who could cause damages to the functioning of a critical infrastructure asset.
4. Responsible entities for critical infrastructure assets must ensure that their risk management program includes details of how the entity manages risks arising from the off-boarding process for outgoing personnel.
(The definition of critical personnel includes, but is not limited to, any employee of a responsible entity with responsibility, access, control or management of the essential components or systems of the asset and whose absence or compromise would prevent the proper function of the asset or could cause significant damage to the asset, as assessed by the responsible entity. The definition of personnel includes, but is not limited to, direct employees, interns, contractors and subcontractors.)
Response: If the responsible entity wishes to undertake background checking through an AusCheck background check, or an alternative, that decision is at their discretion.
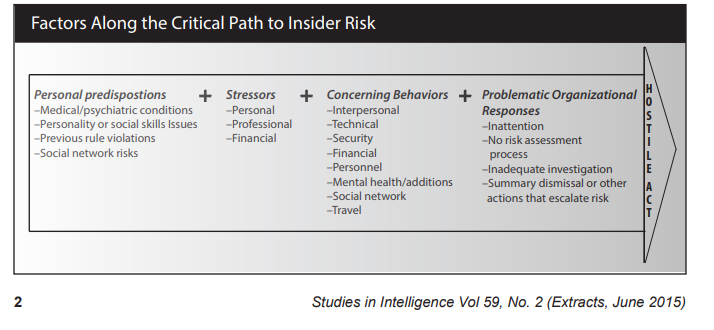
We believe that many CI entities will struggle at navigating Rule 2b and understanding or parsing the difference between an Auscheck (with an ASIO Assessment) on the one hand and an “equivalent vetting check” on the other. (spoiler here). Here is what Keolis Downer AND the Head of Auscheck had to say:

We doubt Keolis Downer’s view that ‘many’ use the PSPF for personnel security measures in practice – but it is recommended by many:

For example the Electricity Sector: The AESCSF Framework Core doesn’t even elevate to Aust Standards for Employment Screening – so we believe that there is a false sense of security at play.
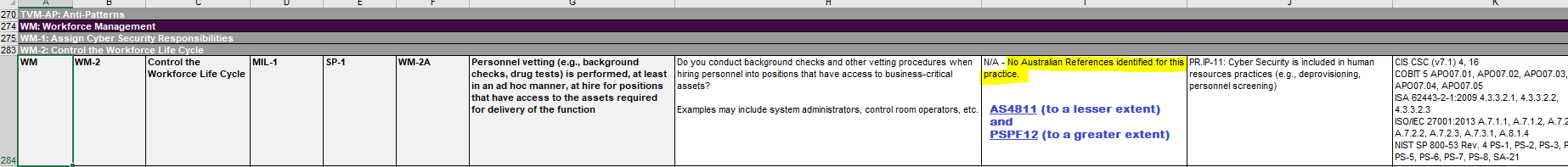
The good news.
Rule 2a and 2b are compatible with Cleard Life’s AS4811-2022 and PSPF-compliant Suitability Assessments – 4 levels for the 4 critical positions
Home Affairs has said that:
“If the responsible entity wishes to undertake background checking through an AusCheck background check, or an alternative, that decision is at their discretion.”
How does Australian Standards 4811-2022 and the PSPF impact these Rules?
These Rules dovetail appropriately into Protective Security Policy Framework – assessing suitability (PSPF12), ongoing suitability (PSPF13) and separating personnel (PSPF14).
The new Australian Standards 4811 – 2022 Workforce Screening now includes the requirement to conduct a suitability interview and risk assessment – a guide can be found here.
How can we help you?
We are a national security clearance processor of Baselines, NV1s, NV2 and PVs.
We are certified as confirming to all 92 of the 92 musts & shoulds for AS4811 Workforce Screening.
We manage AGSVA security clearance portfolios of behalf of our CI clients (AS4811-2022 and PSPF12,13,14 and AS4811:2022) primarily in the Defence Industry.
We are more than able to assist you with your vetting checks and your PERSEC governance, risk and compliance needs.
Section 9 (6) (b) a responsible entity must have regard to whether the CIRMP describes the personnel risks, the occurrence of which could have a relevant impact on the asset. If your organisational risks differ from what the Auscheck CI check covers (eg. drug use, workplace violations, data breaches, suspicious overseas travel and connections, mental health, financial issues) then talk to us.
Solved.
You can even start using Australia’s Critical Infrastructure Clearance today!
Get in touch today.
Other reading:
Critical Infrastructure entities must now hunt for spies.
Critical Infrastructure: Public Submissions React to Trusted Insider Risk Mitigation Options.
Critical Infrastructure: Risk Management Program – Rule 2 now implemented.
_____________________________________________________________________
Extra Info:
What about assessing critical positions?
The definition of critical position includes but is not limited to, a position in a responsible entity which has responsibility, access, control or management of the essential components or systems of the asset and where the absence or compromise of the position or its holder would prevent the proper function of the asset or could cause significant damage to the asset, as assessed by the responsible entity. Here is some general help Occupations and Cleard Life Clearance Levels – a helpful guide and Which Suitability Clearance level is right for your personnel?
What is ‘sensitive’?
Sensitive operational information is information about the asset that includes but is not limited to:
a. layout diagrams;
b. schematics;
c. geospatial information;
d. configuration information;
e. operational constraints or tolerances information; and
f. data that a reasonable person would consider confidential or sensitive about the asset.
source: https://www.homeaffairs.gov.au/reports-and-pubs/files/risk-management-program-rules.pdf