Critical Infrastructure entities must now hunt for spies.
Preemployment screening does not hunt for spies. The PSPF does. We do.

Meet Bruce. He works for your critical infrastructure company. He is like many workers in Australia: born in another country, studied at a great university there but then moved here to make a life for himself. His dad owns and runs a business back home and in fact Bruce is part of it too: he travels home regularly to help out where he can and also catch up with friends and family – his uncle is a member of a political party which is quite special. He stays in touch with family weekly and they discuss many things – from the budding new romantic relationship to the interesting work he does at your company. It’s known that he thinks that his birth country gets some pretty unfair media coverage and knows first hand that ‘it’s not that bad’. One day, a stranger ‘happens’ to bump into him and tells Bruce that he knows his parents and that he saw them just a few weeks ago. The stranger builds rapport. Then, the stranger tells Bruce that his parents and the business will ‘remain safe’ (a subtle threat?) as long as he provides some small insignificant details about his work …
Significant personnel security reforms are taking place. According to Home Affairs’ Critical Infrastructure Centre (CIC) who is tasked to mitigate sabotage, espionage and coercion and other personnel risks, the implementation of Cyber Security Strategy 2020 will usher in enhanced security obligations, legislation and a framework that will impact these sectors:
- Banking and finance
- Communications
- Data and the Cloud
- Defence industry
- Education, research and innovation
- Energy
- Food and grocery
- Health
- Space
- Transport
- Water

As the CIC rolls out the Critical Infrastructure Resilience Strategy they note that there is a “range of hazards that have the potential to significantly compromise the supply of essential services across Australia; personnel and cyber security are all increasingly interrelated.”
Screening personnel for connections and associations with state-based actors makes sense. To probe deep enough to consider if a worker is vulnerable to coercion is a specialist aptitude (technically called counter-espionage) but extremely important from a detection and deterrent perspective. In terms of cyber, IBM & Verizon research note that malicious (not fat finger, or clicking on a wrong link) trusted insiders contribute to 1:4 of all data breaches, costing millions of dollars of damage per breach and this could expose Australia to a catastrophic loss in the critical infrastructure sector. Screening a ‘serial’ data breach offender (or other counter-productive workplace behaviours) is not as easy as checking a centralised database and when detected serious thought must be given about the suitability of that person.
As a Defence Industry Security Program member ourselves and a people risk organisation, we understand why the CIC has highlighted personnel security risks and the central role it plays to identify and understand various types of risks and then mitigate them.

The Protective Security Policy Framework PSPF12 relates to personnel security (PERSEC) and states that all personnel and contractors who have access to government resources, information, people, assets must be suitability cleared. Critical Infrastructure entities will now need to meet this standard. Furthermore, PSPF13 relates to the ongoing suitability of personnel.
Q1. Is suitability defined in the PSPF? Yes. Honesty, Trustworthy, Tolerance, Maturity, Loyalty and Resilience.
Q2. Can suitability be determined by a $50 police check, a referee check, an ID check? No.
Q3. Can the AS4811 Employment Screening -alone- identify and understand sabotage, espionage or coercion risk from a national security perspective? No.
Q4. Are there better practices available to inform employment screening than the 2006 Standard? Yes.
Q5. Do HR or Security sections have the qualifications, experience, dexterity and skillset to investigate, evaluate these issues without bias, without discrimination – in a fast, scalable, standardised way? No.

“Employers should have a robust process for responding to red flags that arise from employment screening checks.”
– ICAC NSW White paper: Strengthening employment screening practices
“Employment screening typically consists of checking a candidate’s identity. There are better practices available to inform employment screening such as the Protective Security Policy Framework (PSPF) & Personnel Security Protocol.”
– ICAC NSW Employment Screening Handbook.
The Cyber problem stated: 1:4 data breaches are malicious & expensive.
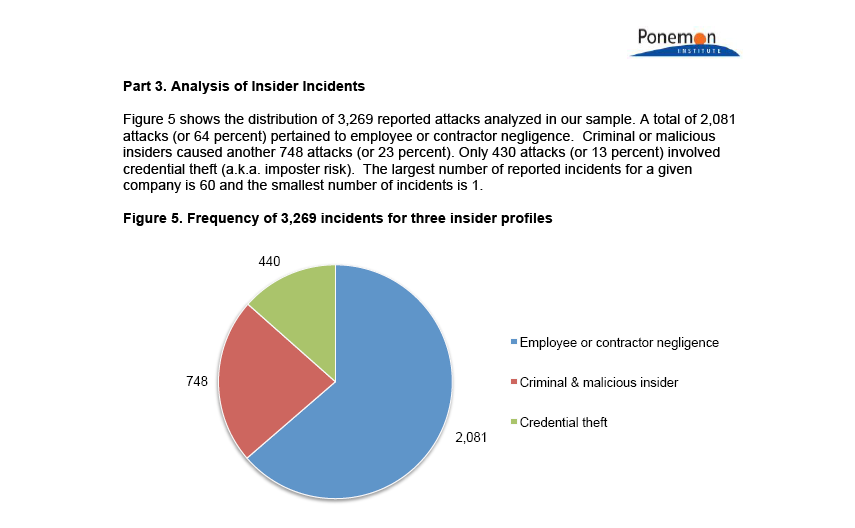
Source: IBM.
The influence problem stated: We are being exploited.
Australia is announcing the danger and risks surrounding the safety and security of key personnel in critical infrastructure sectors.

The Australian government understands how important PERSEC is in our protecting our infrastructure. For example, the Sydney Morning Herald reported that one critical infrastructure sector was a top target in an article titled “Cashed-up ASIO hunting spies at naval shipyards.”
“[ASIO] have emphasised the need to act early to protect the industry, which the government has been told will become one of the nation’s top targets for foreign espionage. Measures will include ***security screening*** for thousands of new employees and supply-chain network security.”
This leads to supply chain security …

However, the Cyber Supply Chain Risk Management Practitioner Guide does not provide clear guidance on best practice as it relates to personnel considerations and refers the reader generally to the PSPF:
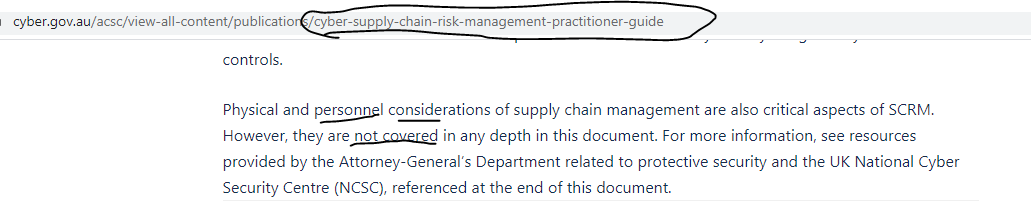
Managing third-party risks can be resolved by applying the same vetting practices and standards used for your staff as contractors; the PSPF. It could be achieved through various mechanisms: obligatory contractual agreements, due diligence tender evaluations, enhanced screening for temporary workers via existing vendor management systems. Interestingly, Glassdoor research indicates that by screening candidates you can achieve a 70% increase in the quality of your workforce – something most employers should be amenable towards: no-one likes the feeling of betrayal and no-one wants to be responsible for letting a ‘bad apple’ in and risk losing the contract or worse.
Compliance to Cyber Security Principle P10 is and will be required in many sector and many industries:”Only trusted and vetted personnel are granted access to systems, applications and data repositories.” The ISM Guidelines for Personnel Security provides ISM Security Control 0434 “Personnel undergo appropriate employment screening before being granted access to a system and its resources.”
If you look further to International Standards, ISO/IEC 27001:2013 – A.7 Human resource security : requirements, you will note that even a police check is not considered required.
A.7.1 Prior to employment
Objective: To ensure that employees and contractors are “suitable” for the roles for which they are considered.”
When an individual is hired for a specific information security role, organisations should make sure the candidate can be trusted to take on the role.
IS0 27001 A.7.1.1 Screening
Control – “Background verification checks on all candidates for employment shall be carried out in accordance with relevant laws, regulations and “ethics” and shall be proportional to the business requirements, the classification of the information to be accessed and the perceived risks.”
Summary: The PSPF is the best standard as it scans 21 dimensions of a person life.
Conclusion: Dexterity, at scale, is a must.
Pre-employment personnel security risk measures (PSPF12), or ongoing suitability (PSPF13) obligations or ‘one-time risk assessment’ or a ‘360 degree cyber audit’ will go a long way to understand the hidden risks that exists in your critical infrastructure company’s current workforce, contractor and supply chains.
An enhanced, fast, reliable, standardised personnel security measure is not only appropriate but essential and mandatory for sovereign resiliency. This element will be included into the risk assessment of critical infrastructure, the framework, and legislation adjustments – including offshore worker risk:

Full implementation should not be a worry. The missing piece is a cleared life.
Cleard Life Vetting Agency has democratised security vetting and created the ability for infrastructure owners and operators to easily and simply access a PSPF-compliant suitability check at the Baseline equivalent, as fast as “next day” – via through the AI-engine and vetting-as-a-service (VAAS) platform.

You can now access the same suitability standard checks which are applied to national security clearances, sped up a 100-fold and at a fraction of the cost.
We are here to assist you with your non-security clearance compliance, vetting and security measures.
We would be pleased to assist you further.
Review the product details page here.
Join now (it’s free for 90 days and your first CL0 Basic Assessment is free, too)
Read more:
60 comments from industry leaders about the state of personnel security:
Critical Infrastructure: Public Submissions React to Trusted Insider Risk Mitigation Options.
AGSVA Baseline vs PSPF Goldilocks Clearance – the requirements compared.
Australia’s first CI Clearance