Cyber Security Risk Audits start to look at the HR workforce. A recent study out of Cylab, 69% of respondents had more than 5 malicious, high-concern insider incidents. 44% of businesses had more than 10 incidents. 11% had more than 100 incidents, such as financial fraud, sabotage, data theft, or workplace violence. In 2021 this trend won’t stop. Cyber security is always going to be […]
Exploring what the right cybersecurity path forward looks like when people are involved. 70,604 cyber security professionals were asked to respond to the question, ‘What Keeps You Awake at Night’, with the option to select one of three possible answers. a. Third Parties b. Insider Threats c. Nation State Actors 55% of cyber professionals are worried about their own staff, their own colleagues. This echoes what Terry Halvorsen, the former CIO of the US Department of Defense, said in recent Sydney conference: “The single threat to your system is people. Some of it is not even malicious. People ask what keeps me up at night? It’s people.” He then recommended business leaders to spend their cyber budget on people – before tech. That is an important statement from a person who controlled a USD 42 Billion annual budget. Background: Low hanging fruit are external people. The typical corporate network topography is wide and that means a lot of potential entry points if left unsecured or vulnerable. The work from home (WFH) trend has exacerbated this. The last thing any senior leader needs is the fallout from a major security breach or attack. We are seeing near daily headlines littered with cyber breach incidents and ransomware of well-known brands. Closer to home they might even be third party supply chain partners. Internal threats can cost many times more than an external attack. Cyber professionals are aware that staff are normally, by default, accessing sensitive networks and information from anywhere, for the foreseeable future. The climate in which potential internal breaches – negligence or intentional – is elevated. Tech solutions try to secure all the hardware that the internal user accesses. This is difficult when trusted employees WFH and use unsecured home computers, home printers, home USB sticks etc. Other tech solutions include user behaviour motioning software to detect and alert when internal people are in the corporate network system and doing the wrong thing. The role of trust cybersecurity […]
The security expert has three reasons why you should never charge your phone at an airport – Callum Jones (via unilad.com) A security expert has warned tourists against charging their mobile phones at an airport. After many hours of checking directions, seeing where you need to go once you land at your arrival destination, […]
1. Introduction With insider threats posing a significant challenge in the Health industry, it is imperative to establish rigorous user screening processes that align with Australian Standard 4811-2022 and Protective Security Policy Framework (PSPF) 12, ensuring the security and integrity of commonwealth systems – such as the My Health Record system. This article highlights the […]
Learn how improved reporting by peers, family, and social contacts can help prevent insider attacks and protect your organization’s IT systems and data. Insider threats can pose a significant risk to an organization’s IT systems and data. These threats can come from current or former employees, contractors, or business partners who have authorized access to […]
Critical Infrastructure entities must now hunt for spies. Preemployment screening does not hunt for spies. The PSPF does. We do. Meet Bruce. He works for your critical infrastructure company. He is like many workers in Australia: born in another country, studied at a great university there but then moved here to make a life […]
Security Awareness briefings for every candidate. It is important for employers to know and understand that candidate’s background is not filled with unmitigated risk. However, new employees to the organisation might not fully understand or comprehend the employer’s security posture and culture. That’s where a security & cyber awareness mini course comes in. After the […]
Trusted insiders are potential, current or former employees or contractors who have legitimate access to information, techniques, technology, assets or premises. Trusted insiders can intentionally or unknowingly assist external parties in conducting activities against the organisation or can commit malicious acts of self-interest. Such action by […]
The Australian Government is developing our nation’s next Cyber Security Strategy as part of its commitment to protecting Australians from cyber threats. The new strategy will be a successor to Australia’s landmark 2016 Cyber Security Strategy, which set out the Government’s 4 year plan to advance and protect our interests online backed by a $230 […]
Preemployment ‘Best Practice Guide’ for Social Media Screening. A digital footprint is the unique pattern of electronic transactions made by an individual’s publicly accessible online presence. An assessment of an individual’s digital footprint can provide insight into their life, interactions and personal views. This information may identify behaviours of concern or provide further assurance that […]
We saw this in the news recently “The NSW cyber security agency is extending its scope to cover councils and small agencies.” (https://www.governmentnews.com.au/cyber-security-nsw-to-extend-scope-to-councils) “Customer service minister Victor Dominello on Wednesday announced a three-year, $60 […]
Are you Naked? Is Cyber Insurance a Must? * 15% of SME’s have cyber insurance. * 1.955 million Australian businesses are not insured. * 70% percent of all businesses are unprepared for a cyber-attack. * 34% of breaches involve malicious internal actors. * 59% of orgs experience at least one malicious insider attack over […]
When it comes to personnel and IT, it’s a high-risk environment right now. 9 in 10 data breaches involve trusted insiders – mainly to due to negligence 1 in 5 data breaches are caused by malicious employees 1 in 5 lie on their job resumes 1 in 5 had misrepresented their qualifications 3 in […]
Joseph Steinberg is a cybersecurity expert and entrepreneur who founded the information security companies, Green Armor Solutions and SecureMySocial. He invented several popular cybersecurity technologies in use today, writes a column on cybersecurity for Inc., and is the author of several books on information security. Q. “In general, the greatest data security risk is posed […]
A Hypothetical one Sided Phone call between friends, goes something like this: Caller A: So, what’s your security strategy? Caller A: What do I mean? Well, IBM says 44.5% of breaches are caused by malicious trusted insiders. Not fat fingers, not clicking on a wrong hyper-link, not accidents, not Russian hackers. Intentional. Caller A: So let me […]
Digital Innovation: Australia’s $315b opportunity. The new report from Alpha Beta for CSIRO/Data61, called “Digital Innovation: Australia’s $315b opportunity” identifies eight strategic areas where Australian businesses can succeed in creating new digital products or services. These opportunities are precision healthcare, digital agriculture, data-driven urban management, cyber-physical security, supply chain integrity, proactive government, legal informatics and […]
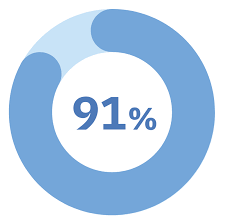
In an Ohio-based Employers Resource Association* survey… 91 percent are using background checks. That seems high. But what s.p.e.c.i.f.i.c.a.l.l.y. does that mean? A Google search? Police check? Facebook search? LinkedIn page view? A 2 minute call to the a previous boss? But more importantly, what do you do when you receive an adverse result? To […]
Marc Weaver Databasable is an IT consultancy firm that provides database administration support and specializes in moving your databases and applications into the cloud. Founded by Marc Weaver in 2015, databasable uses his vast employment experience from large financial institutions in London, Sydney, and New York. “Obviously a data security breach from an outsider will result […]
GREG MANCUSI-UNGARO @BrandProtect Greg Mancusi-Ungaro is responsible for developing and executing the BrandProtect market, marketing, and go-to-market strategy. A passionate evangelist for emerging technologies, business practices, and customer-centricity, Greg has been leading and advising world-class marketing initiatives, teams, and organizations for more than twenty-five years. Prior to joining BrandProtect, Greg served in marketing leadership roles at […]
CHRISTOPHER BURGESS @burgessct Christopher Burgess is the CEO, President and co-founder of Prevendra. He is an author, speaker, advisor, consultant, and advocate for effective security strategies, be they for your company, home, or family. “The most serious threat to a company’s data security is the…” Insider threat, which comes in two forms: The malevolent insider is […]
STEVE DURBIN @stevedurbin Steve Durbin is Managing Director of the Information Security Forum (ISF). His main areas of focus include the emerging security threat landscape, cyber security, BYOD, the cloud, and social media across both the corporate and personal environments. Previously, he was Senior Vice President at Gartner. “As data breaches increase, many will be the […]
JAMES GOODNOW @JamesGoodnow James Goodnow is a brilliant, creative, compassionate attorney and a technology aficionado in Phoenix, Arizona who’s been named one of America’s Techiest Lawyers by the ABA Journal, the official publication of the American Bar Association. Apple actually selected him as the first lawyer to be featured in one of its commercials, and also […]
Among 874 incidents, as reported by companies to the Ponemon Institute for its recent Cost of Data Breach Study, 568 (65%) were caused by employee or contractor negligence; 85 (10%) by outsiders using stolen credentials; and 191 (22%) by malicious employees and criminals. Data breach cost per breach $2.5 million. The report goes on to […]
There are serious consequences of non-compliance. Where an organisation breaches a mandatory notification requirement, the contravention is deemed to be an ‘interference with the privacy of an individual.’ As a result, it may amount to a breach of a civil penalty provision of the Privacy Act. This could result in the organisation being liable for […]