Are you Naked? Is Cyber Insurance a Must?
* 15% of SME’s have cyber insurance.
* 1.955 million Australian businesses are not insured.
* 70% percent of all businesses are unprepared for a cyber-attack.
* 34% of breaches involve malicious internal actors.
* 59% of orgs experience at least one malicious insider attack over the last 12 months.
The Attorney General George Brandis once said:
Most personnel strive to conduct themselves in an ethical and professional manner. However, it would be negligent to ignore the risk of someone deliberately causing harm or exploiting their positions of trust. The ‘trusted insider’ represents a real and enduring risk to everyday business practices. It is an important risk consideration for both Government and the private sector. Insider activity is at the very least embarrassing and damaging to an organisation’s reputation, but it can also be disruptive, expensive and life threatening.
If you were an insurance provider there seems to be a lot of business to write, but given the sobering statistics you might not be in business for long!
“Insurers must either get involved in cyber insurance or see their business fail in the years ahead” – Maarten van Wieren, Cyber Risk Quantification Leader, Deloitte (now Managing Director, Aon Risk)
A policy-holder’s cyber security risk profile is a combination of (1) the value of its intellectual property (measured both in quantitative monetary and qualitative security terms), (2) how likely external & internal threat actors are to target them, and (3) the attributes of the policy-holder’s computer systems. Insurance providers can establish evidence-based best practices potentially providing discounted premiums to induce an improved baseline level of cyber hygiene.”
In underwriting policies, cyber insurance firms would ideally assess the second point above – that is, behaviours of a customer’s employees as part of its risk profile. In the past, doing so has been challenging. Quantifying and reducing human error is hard, but crucial none-the-less. As policyholders gain greater clarity and management of their human risks, they can demonstrate remediation actions that will reduce risk. Cyber insurance therefore plays an important catalyst role in the digital age.
Efficient pricing of cyber-insurance policies is currently very difficult. This results in higher than necessary cyber-insurance premiums for Australian businesses, lower than optimal claim limits, wider than necessary exclusions and limited carve-backs in policy wordings. One of the major contributing factors to this inefficiency in cyber-insurance policies is the immaturity of the actuarial models which are used to price such insurance. Cyber-insurance models suffer from a lack of access to rich historical datasets of losses, and to information about the cyber-maturity capabilities of the policy-holders prior to them suffering those losses. By collecting personnel risk information would improve the efficiency of the Australian cyber-insurance market, potentially lowering premiums for Australians.
For both cyber insurance underwriters and policy-holders, the answer is the same: greater clarity about cyber risk, and more effective action to reduce the malicious insider threats that cause or contribute to most security compromises. New certifications (such as the ISM, ASD Essential 8, PSPF-compliant PERsonel SECurity) with strict criteria are being developed, designed to help organisations make well informed cybersecurity decisions, and have greater clarity and confidence in navigating the complex cybersecurity marketplace.
“With an increasing array of security standards fleshing out what reasonable steps might entail, directors failing to protect data could risk negligence lawsuits due to a failure to protect data from a “reasonably foreseeable” risk of harm.” – “Australian Wastes its Cyber Spending, ACS
Already we are seeing B & O’s insurance premiums escalating. Therefore the introduction of a screening/vetting evaluation program that uses government suitability standards (PSPF PERSEC) allows, for the first time, a whole-of-company ‘insider’ vulnerability risk assessment to be conducted. Vetting personnel, contractors and third party supply chains will increase the visibility and actionable intelligence. The policyholder can demonstrate an improved cyber risk posture. Importantly, it is will be a determining factor for cyber risk insurance premiums.
Birthed out of a national security vetting background, Cleard Life Vetting Agency (CLVA) has products and services that are an effective way in reducing cyber insider risk and CLVA is a catalyst for PERSEC for any cyber solution. Policyholders that adopt CLVA’s solutions may qualify for enhanced terms and conditions on cyber insurance policies from insurers.
CLVA: Six features that will boost your Cyber Hygiene and Cyber Insurance attractiveness.
1. Reduction of cyber risk: demonstrated ability to address major enterprise cyber risk such as data breach, theft or corruption; business interruption; or cyber extortion.
National security clearance processes are necessary, extensive but remain prohibitively lengthy and expensive – eg. The top-level clearance costs more than $11,000 per check and a ‘complex case’ on average takes 792 days to reach a decision. They are also not available to civilians. Most security personnel vetting programs around the world now use the ‘critical path to insider risk’ protocol which evaluates candidates background for specific personal predispositions, stressors and concerning behaviours. It predicts or anticipates a trusted insider threat with great efficacy.
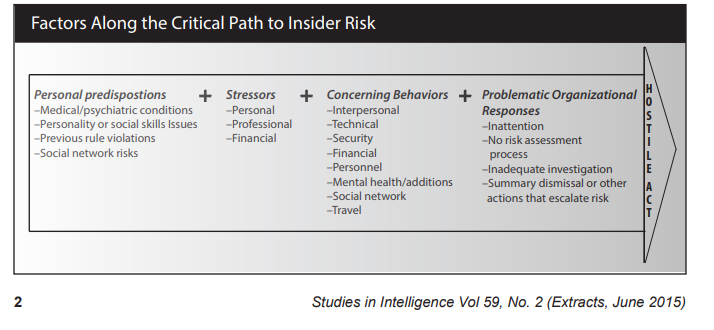
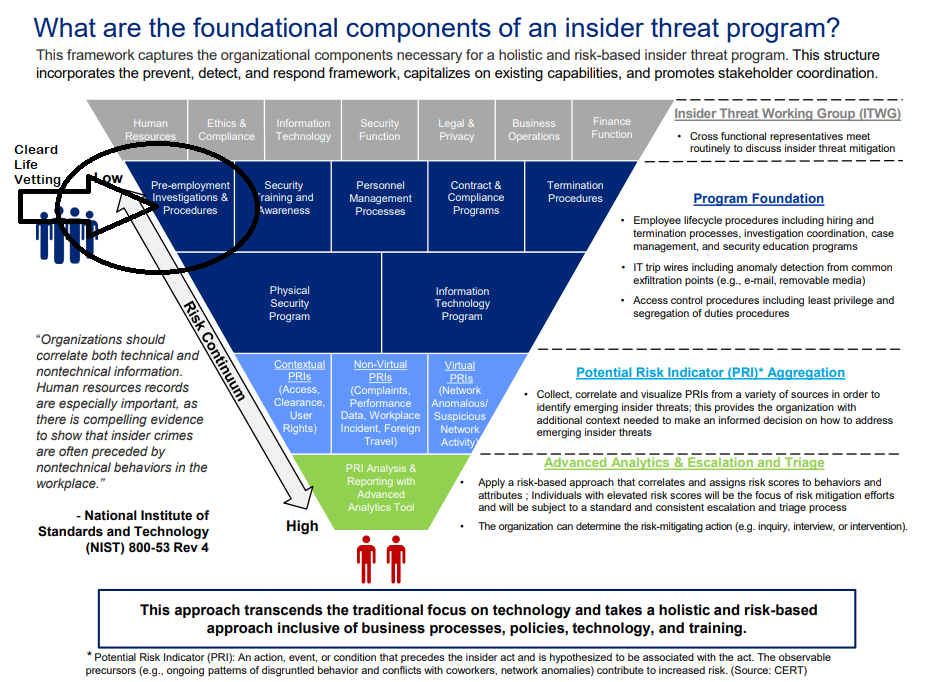
The CLVA scan detects ‘unsuitable’ people accessing highly sensitive, personally identifiable, commercial sensitive, or classified information. The identification of the combination of ‘motive and opportunity’ to undertake a hostile act (or some other counter-productive workplace behaviour) provides everyone greater clarity about insurance risks. Therefore, the practice and the remediation of red/orange flags reduces cyber risk considerably.
2. Key performance metrics: demonstrated ability to quantitatively measure and report on factors that reduce the frequency or severity of cyber events.
In conjunction with the critical path protocol, evaluating a workforce for character and integrity also means addressing seven factor areas (21 sub areas) used in national security clearance processes including the non-discriminatory adjudicative guidelines s (Protective Security Policy Framework – Personnel Security – PERSEC). This includes security violations, mental health, substance use, financial considerations to name a few. CLVA uses proprietary AI software to undertake candidate investigations, the whole-of-person analysis and through supervised learning algorithms, assists with creation of timely recommendations.
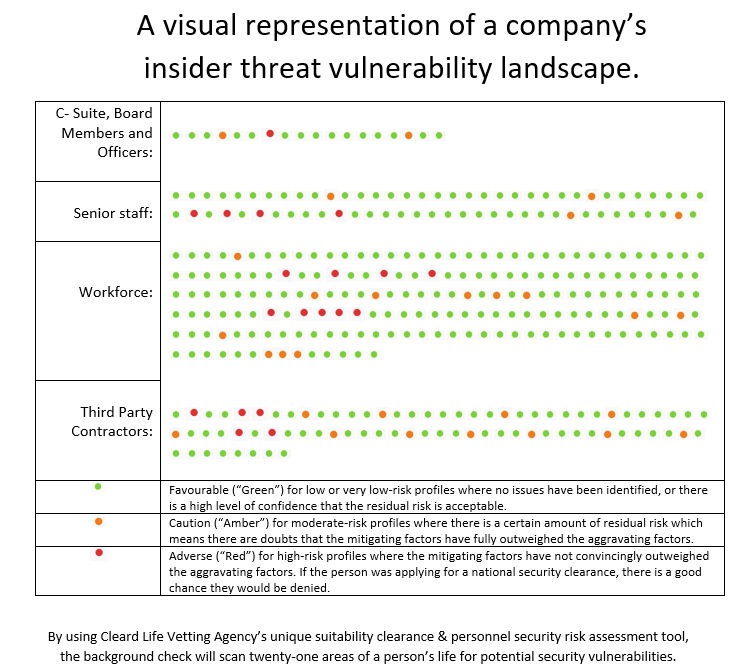
3.Viability: client-use cases and successful implementation.
CLVA has a 24/7 vetting-as-a-service platform so that implementation is easy to carry out. Users create an assessment at any time, the candidate is then contacted immediately for the interview to begin 24/7. The result can be completed as-fast-as next business day and the cost as-low-as $135 per assessment. The ability to deeply understand not only the red or amber lights, but also see, in aggregate, which areas of the organisation needs to be addressed and remediated is especially helpful. We are working with Cyber Indemnity Solutions (Crimson Risk) and Avantia Cyber Security consulting firms and many others are following suit.
4. Efficiency: demonstrated ability of users to successfully implement and govern the use of the product to reduce cyber risk.
The solution reveals hidden risks and highlights weak areas. By drilling down to aggregated factor areas results, users can take action or use CLVA consultants who can offer risk mitigation advice, tools and board level presentations and recommendations. Actions might include adjusting HR policies & practice, or training staff, or setting up an employee assistance program, or social media monitoring etc.
5. Flexibility: broad applicability to a range of companies/industries.
CLVA is industry agnostic and a broad user-base already exists for security vetting. Why? Because people are same wherever you go. Patterns without pivots are important. Rule-breaking behaviour outside of the workplace tends to become rule breaking behaviour inside the workplace. Serial data breaches tend to be ‘lax’ again. Untreated mental health concerns have security implications. The CLVA AI engine also has direct implications for national security vetting efficiency and also state-based screening units implications that could reduce determination time-frames considerably.
6. Differentiation: distinguishing features and characteristics.
Even though malicious insiders are blamed for a large proportion of breaches (IBM research has the percentage as high as 44.5%), PERSEC has been the missing link in the marketplace. It has been either ignored or dismissed as too hard. There has never been a non-discriminatory, standardised suitability clearance that has the speed, accuracy, affordability, or scale – until now. The user (be it a cyber consulting company or the organisation directly) now has the option to complete a one-time audit, periodic check-ups for the current workforce, change-of-circumstance evaluations, inclusion into preemployment procedures for cyber hygiene, vetting of third party personnel and/or tender shortlisting due diligence.
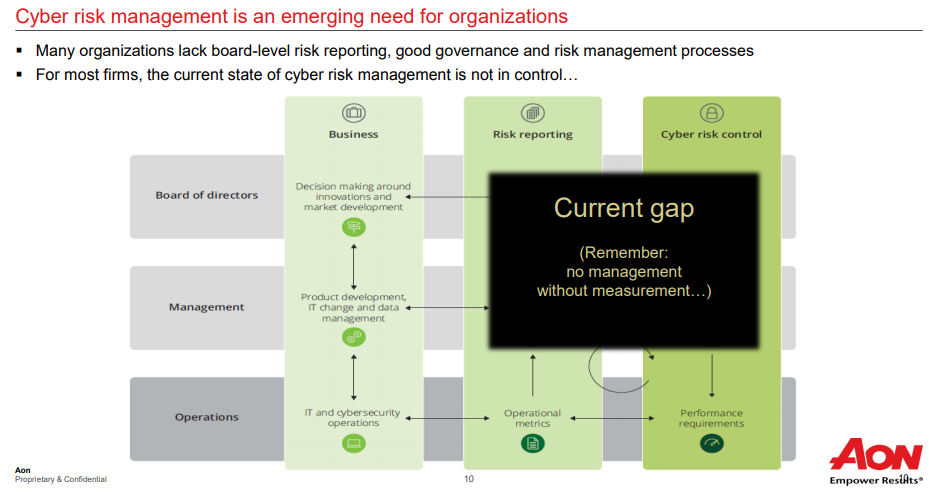
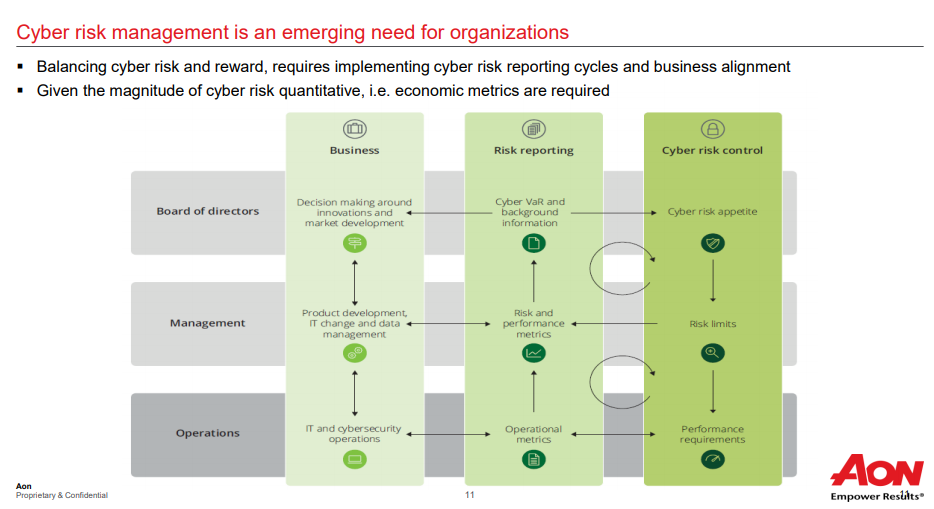
Board of Directors
For centuries, insurance has empowered enterprise by making new forms of risk more manageable. Cyber insurance plays an important role in the digital age. By gaining greater clarity about the hidden human risk that exists inside your organisation, you will have better ways to report it, control it and make decisions to reduce it.
Managing Director, Aon Risk, Maarten van Wieren public presentation.
Conclusion
Research says you can detect early indicators of a hostile act before they happen. We know its true.
We look forward to serving you and helping with your insider threat program, organisational vulnerability screen, cyber insurance needs and ways to improve your cyber hygiene.
Get in touch today sales@cleard.life or 02-6171-4171!