Exploring what the right cybersecurity path forward looks like when people are involved. 70,604 cyber security professionals were asked to respond to the question, ‘What Keeps You Awake at Night’, with the option to select one of three possible answers. a. Third Parties b. Insider Threats c. Nation State Actors 55% of cyber professionals are worried about their own staff, their own colleagues. This echoes what Terry Halvorsen, the former CIO of the US Department of Defense, said in recent Sydney conference: “The single threat to your system is people. Some of it is not even malicious. People ask what keeps me up at night? It’s people.” He then recommended business leaders to spend their cyber budget on people – before tech. That is an important statement from a person who controlled a USD 42 Billion annual budget. Background: Low hanging fruit are external people. The typical corporate network topography is wide and that means a lot of potential entry points if left unsecured or vulnerable. The work from home (WFH) trend has exacerbated this. The last thing any senior leader needs is the fallout from a major security breach or attack. We are seeing near daily headlines littered with cyber breach incidents and ransomware of well-known brands. Closer to home they might even be third party supply chain partners. Internal threats can cost many times more than an external attack. Cyber professionals are aware that staff are normally, by default, accessing sensitive networks and information from anywhere, for the foreseeable future. The climate in which potential internal breaches – negligence or intentional – is elevated. Tech solutions try to secure all the hardware that the internal user accesses. This is difficult when trusted employees WFH and use unsecured home computers, home printers, home USB sticks etc. Other tech solutions include user behaviour motioning software to detect and alert when internal people are in the corporate network system and doing the wrong thing. The role of trust cybersecurity […]
Are you Naked? Is Cyber Insurance a Must? * 15% of SME’s have cyber insurance. * 1.955 million Australian businesses are not insured. * 70% percent of all businesses are unprepared for a cyber-attack. * 34% of breaches involve malicious internal actors. * 59% of orgs experience at least one malicious insider attack over […]
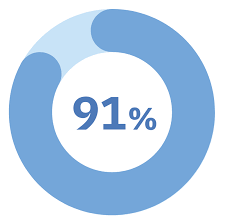
In an Ohio-based Employers Resource Association* survey… 91 percent are using background checks. That seems high. But what s.p.e.c.i.f.i.c.a.l.l.y. does that mean? A Google search? Police check? Facebook search? LinkedIn page view? A 2 minute call to the a previous boss? But more importantly, what do you do when you receive an adverse result? To […]
1 in 4 potential employees admit to behaviours that most employers consider high-risk. HR Managers and Risk Managers need to get onto the same page. Independent university studies have demonstrated the value of integrity tests that screen for hostility, drug and alcohol abuse, theft and lying in the pre-employment phase. But these tests have yet […]
Frank Russo, senior vice president of risk and legal affairs and privacy officer for Irvine, California-based elder care firm Silverado, is always on the lookout for creative ways to mitigate risk. So he was intrigued when he read the “staggering” results featured in a university study about integrity testing. He began exploring how the […]
There are serious consequences of non-compliance. Where an organisation breaches a mandatory notification requirement, the contravention is deemed to be an ‘interference with the privacy of an individual.’ As a result, it may amount to a breach of a civil penalty provision of the Privacy Act. This could result in the organisation being liable for […]