Empowering Education: Leveraging UFIT Protocols for Critical Infrastructure Rule 2 Compliance and DISP Pre-employment Screening
In today’s internationally interconnected world, protecting our critical infrastructure is more important than ever. Universities, as centers of learning and innovation, play a crucial role in this landscape. They must adhere to stringent regulations to protect sensitive information and assets. Research security is the hot topic. The University Foreign Interference Taskforce (UFIT) protocols are designed to help educational institutions navigate this threat while meeting the requirements set out in SOCI Critical Infrastructure Rule 2 and the Defence Industry Security Program (DISP) pre-employment screening, of which most Universities are part of. This article explores how to strengthen your personnel security protocols against foreign interference and other security risks.
Understanding UFIT Protocols
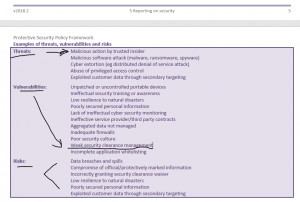
UFIT protocols are comprehensive guidelines that enhance the security and integrity of universities. They provide a structured approach to managing foreign interference risks through due diligence, risk assessments, and continuous management practices. These protocols are essential for safeguarding the educational sector against potential threats.
UFIT Guideline 3.2 Universities conduct due diligence to inform decision-makers of foreign interference risks. Due diligence is conducted on university staff and research students who are at risk of foreign interference.
UFIT Guideline 3.2.1. Universities conduct due diligence on partners and personnel. Additional checks to further assess and understand potential partners and personnel where indicated by identified risk, may include:
ownership structure and management
controlling interests
business registration
background
board members and directors
history of legal issues
Meeting Critical Infrastructure Rule 2 Objectives
Governance and Risk Frameworks
UFIT protocols recommend establishing robust governance frameworks. Universities should develop policies and procedures that outline responsibilities for managing foreign interference risks. These frameworks help ensure that risk management strategies are proportionate to the threats faced, protecting the institution’s people, information, and assets.
Communication, Education, and Knowledge Sharing
Effective communication and education are key components of UFIT protocols. Universities must create communication plans and education programs that raise awareness about foreign interference risks. Training for staff and students engaged in international collaborations is crucial for identifying and mitigating potential threats. By promoting a culture of awareness and resilience, universities can better protect themselves.
Due Diligence and Risk Assessments
Due diligence is central to UFIT protocols. Universities should conduct thorough due diligence on partners and personnel, especially those involved in high-risk areas like research and technology. This includes assessing ownership structures, management, controlling interests, and backgrounds of board members and directors. Continuous evaluation and updating of due diligence processes are necessary to address emerging risks.

Enhancing DISP Pre-employment Screening
The Defence Industry Security Program (DISP) sets high standards for security in the defense sector, and its principles are increasingly relevant to educational institutions – many who are DISP Members.
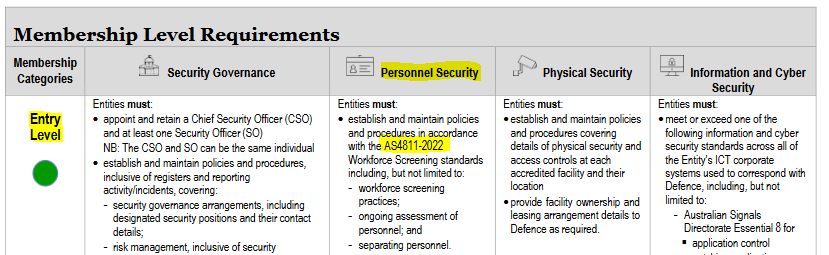
And PSPF:
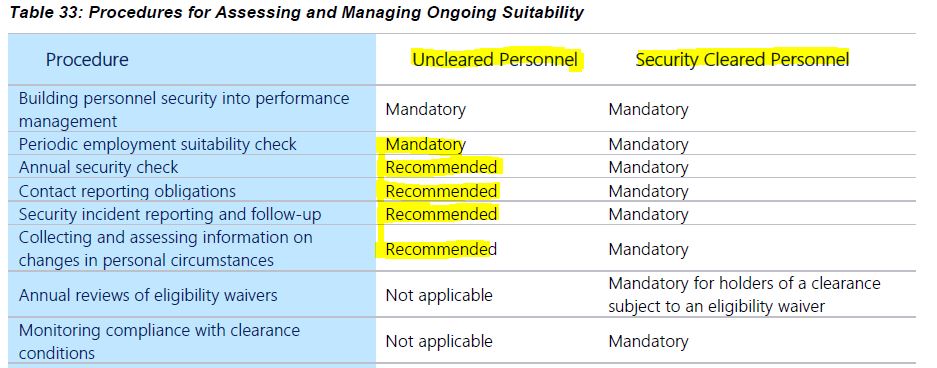
UFIT protocols can embrace DISP pre-employment screening through:
- Comprehensive Background Checks: Conduct thorough background checks to identify potential risks associated with foreign affiliations or influences.
- Risk-Based Assessments: Implement risk-based assessments to determine the level of scrutiny required for different positions.
- Ongoing Monitoring and Reporting: Establish mechanisms for continuous monitoring and reporting to address any changes in an employee’s circumstances promptly.
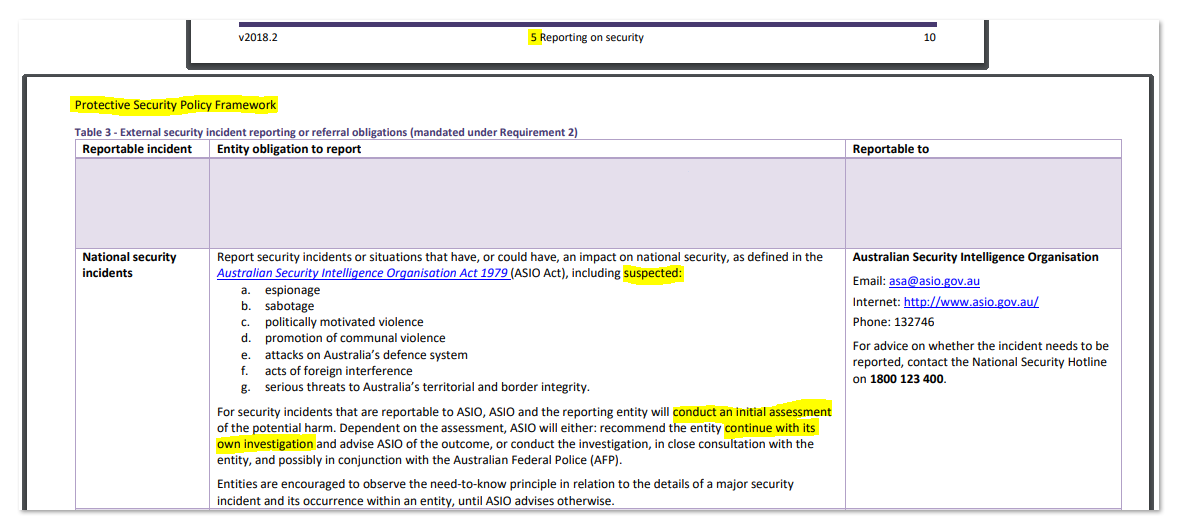
The ASIO Contact Report Scheme and PSPF 5
The Contact Report Scheme is an essential component of the Protective Security Policy Framework (PSPF), specifically aligning with PSPF 5, which focuses on security governance for government entities. This scheme requires individuals within organizations to report any suspicious or unexpected contact from foreign nationals or entities. By integrating the Contact Report Scheme, universities can enhance their foreign interference risk management, ensuring that any unusual interactions are promptly reported and assessed for potential security threats.
PSPF 5 emphasizes the importance of having robust security governance structures in place. For educational institutions, adopting the Contact Report Scheme at the preemployment screening level means establishing clear policies and procedures for reporting and managing foreign contacts. This proactive approach not only helps in identifying and mitigating risks early but also aligns with the broader goals of the PSPF, ensuring that universities maintain high standards of security and integrity in their operations.
The personnel security ecosystem: achieving a positive security culture
ASIO may ask you: Do your recruitment and organisational suitability processes give you confidence your candidate will succeed through vetting? Does your candidate meet clearance eligibility criteria? Does your pre-employment screening indicate compliance with workplace policies and positive security behaviours?
With Cleard Life, the answer is yes.
Practical Steps for Implementation
Develop a UFIT-Aligned Risk Management Framework
Start by developing a risk management framework that aligns with UFIT protocols. This framework should outline foreign interference risks and corresponding mitigation measures. Regular internal reviews and audits are essential to maintain effectiveness.
Train and Educate Staff and Students
Invest in comprehensive training programs for staff and students. These programs should cover identifying foreign interference risks, reporting mechanisms, and maintaining academic freedom and integrity.
Conduct Thorough Due Diligence – early and often.
Implement rigorous due diligence processes for (a) new hires, (b) those moving into Defence-related research programs and (c) research partnerships. This includes detailed background checks and individual risk assessments.

Establish clear escalation pathways for addressing identified risks. This means not just an ID check, a police check or international police check – but checking for foreign influence, loyalty, overseas activities, official contacts and interference.
Leverage Personnel Security Experts to implement these changes
Utilizing resources provided by government agencies, such as the Australian Cyber Security Centre (ACSC) and the Counter Foreign Interference Taskforce will provide you great direction. These agencies offer valuable guidance and support for implementing UFIT protocols and enhancing cybersecurity measures. However, you will more than likely need a Trusted Partner – like Cleard Life – to be satisfied with your governance, risk and compliance goals.
Conclusion
By adopting UFIT protocols with Cleard Life, educational institutions can significantly enhance their ability to meet Critical Infrastructure Rule 2 objectives and DISP pre-employment screening requirements. These protocols provide a comprehensive approach to managing foreign interference risks, ensuring that universities remain secure while fostering innovation and global collaboration. In a world where security and openness must coexist, UFIT protocols offer a pathway to achieving this balance.